Anka Build Cloud Controller & Registry Version 1.33.0
Code/Explicit Flow OIDC support
Customers must ensure their provider supports Code/Explicit Flow before upgrading.
ENV ANKA_OIDC_CACHE_TTL has been deprecated.Starting in this version we have removed the Implicit Flow support for OIDC users. This is a major change, but should modernize and increase the security drastically for your cloud. Read more here.
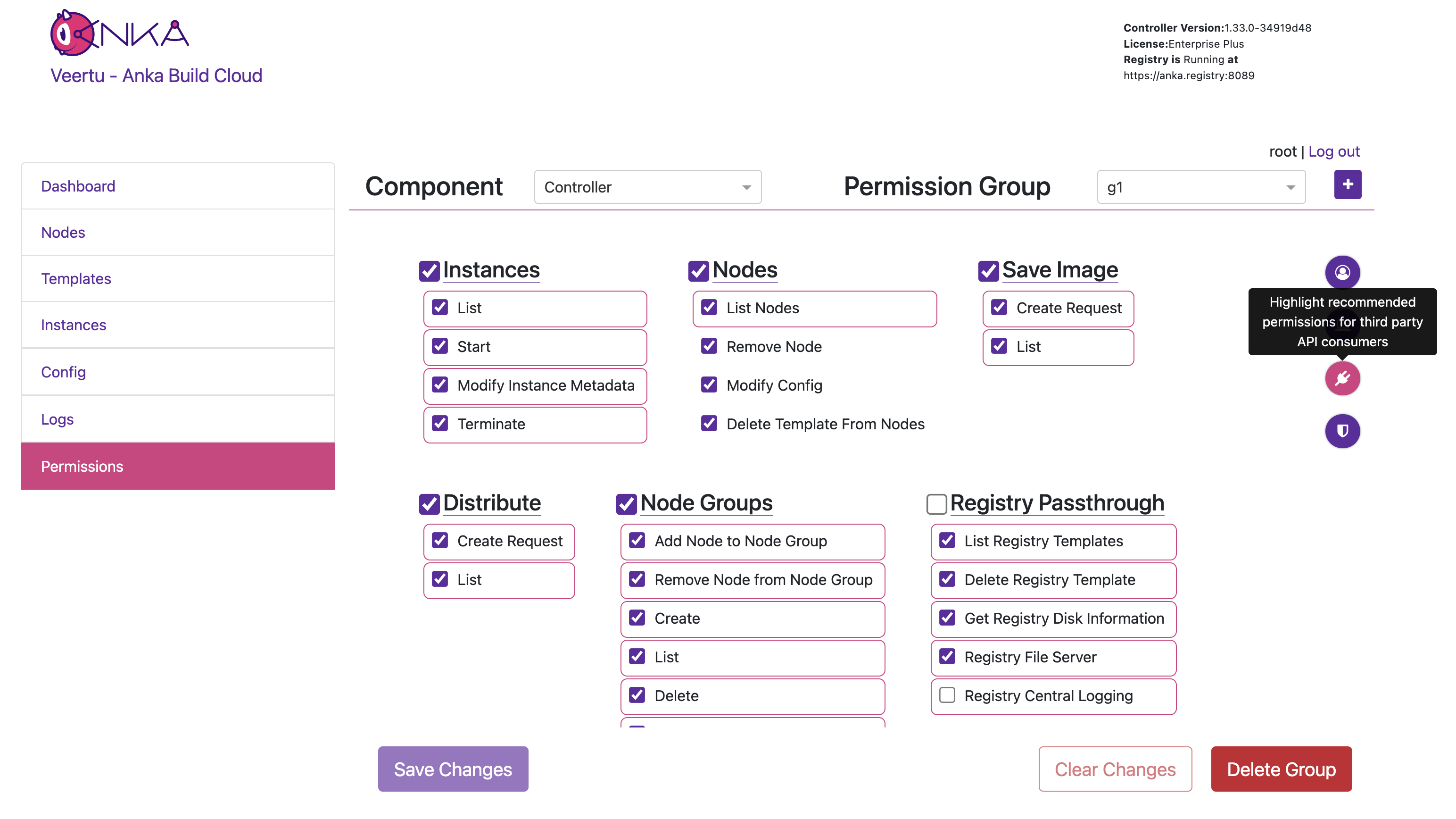
New Permissions Management Panel
The previous admin/ui page has been replaced with a new /#/permission-groups location on the Controller, visible from the dashboard when logged in to a user with appropriate permissions to manage. There are also helper button on the right which will highlight the recommended permissions to add for the specific use-case you have (Node communication, API clients, etc).
Support Certificate Auth with for NGINX Ingress in Kubernetes
Available in Controller >= 1.33.0
Customers who rely on NGINX Ingress controllers which terminate the HTTPS connection inside of the cluster will be able to now pass through TLS headers used for Controller & Registry communication with Certificate Auth.
- This feature requires
ANKA_ENABLE_AUTH: "true"andANKA_ENABLE_INGRESS_NGINX: "true"env vars or corresponding flags to be specified. When these flags are enabled controller/registry will checkSsl-Client-CertandSsl-Client-Verifyheaders (enabled bynginx.ingress.kubernetes.io/auth-tls-pass-certificate-to-upstream: true). For successful authentication,Ssl-Client-Verifyhas to be exactlySUCCESSandSsl-Client-Certhas to contain an url encoded pem certificate. - The ingress controller should be configured to perform SSL client authentication on its own – See here and here. Note that its required to have
nginx.ingress.kubernetes.io/auth-tls-pass-certificate-to-upstreamset totrue. This will enable passing of client certificate to the controller/registry. - This whole setup implies that ingress controller performs SSL termination of all traffic inside the cluster is regular unencrypted HTTP, controller/registry will not validate received certificate, it will trust it by default, because all traffic authentication/validation is performed by nginx.
Here is an example ingress config:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: anka-controller-registry-ingress
annotations:
nginx.ingress.kubernetes.io/auth-tls-verify-client: "on"
nginx.ingress.kubernetes.io/auth-tls-pass-certificate-to-upstream: "true"
nginx.ingress.kubernetes.io/auth-tls-secret: "default/ca-secret"
nginx.ingress.kubernetes.io/auth-tls-verify-depth: "1"
nginx.ingress.kubernetes.io/auth-tls-error-page: "http://ingress-certificate-validation-failed.local"